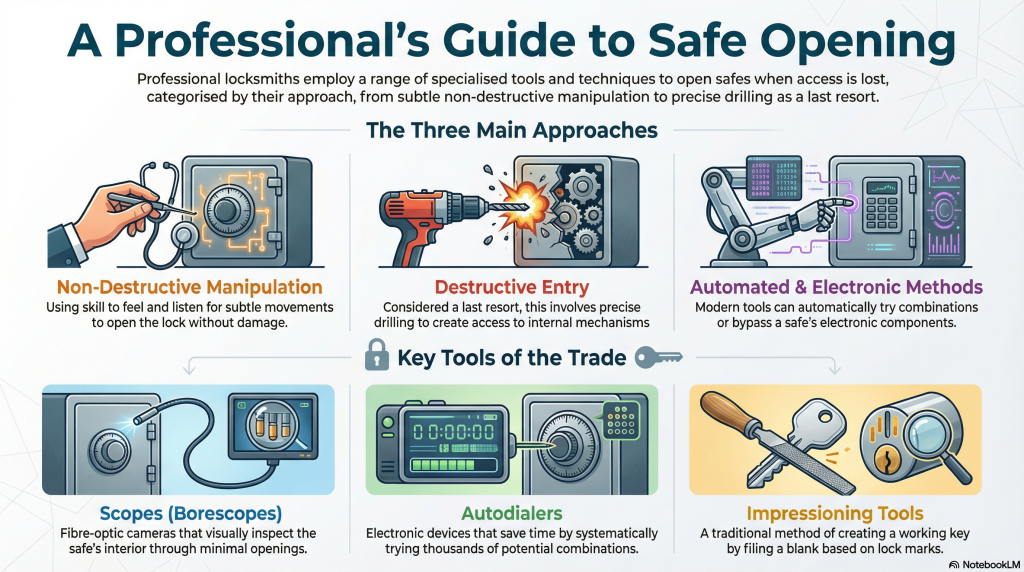
Introduction to Safe Cracking Tools
Safes protect valuables from theft. Locksmiths use specialized tools to open safes when keys are lost, combinations are forgotten, or the safe malfunctions. This guide covers the tools locksmiths use, emphasizing professional service and security.
Key Points
- ✓Drills – Create access points to manipulate internal mechanisms.
- ✓Scopes – Visually inspect the safe’s interior with minimal damage.
- ✓Manipulation Tools – Subtly manipulate the safe’s locking components.
- ✓Autodialers – Automate trying numerous safe combinations.
- ✓Pullers – Remove the safe dial to access the spindle.
- ✓Impressioning Tools – Create a working key by taking a lock impression.
- ✓Bypass Tools – Circumvent the locking mechanism without damage.
- ✓Diagnostic Equipment – Identify lock type and potential vulnerabilities.
Detailed Breakdown
| Aspect | Details | Notes |
|---|---|---|
| Drills | High-speed drills with specialized bits for hardened steel. | Choose the right bit to avoid damaging internal components. |
| Drill Bits (Carbide) | Hard, durable, and cuts through hardened steel plates. | Essential for safes with anti-drill plates. |
| Drill Rigs | Provide stability and precision when drilling. | Ensures accurate drill hole placement. |
| Scopes (Borescopes) | Fiber optic cameras for internal viewing without extensive drilling. | Helps identify the locking mechanism and bypass points. |
| Manipulation Picks | Specialized tools to manipulate safe lock components. | Requires extensive training and experience. |
| Autodialers | Electronic devices that automatically try combinations. | Reduces time to open a safe with a forgotten combination. |
| Pullers (Dial Pullers) | Remove the dial for spindle access. | Allows spindle manipulation and potential lock bypass. |
| Impressioning Files | File down a blank key based on lock impressions. | A traditional method requiring patience and skill. |
Safe Drilling Techniques and Tools
Drilling is a last resort. Locksmiths use precise techniques and tools to minimize damage and access the safe’s contents. Understanding drill types and bits is crucial.
Key Points
- ✓Pilot Holes – Ensure accuracy and prevent drill bit wandering.
- ✓Carbide Bits – Essential for hardened steel plates and anti-drill mechanisms.
- ✓Coolant – Prevents overheating and extends drill bit life.
- ✓Drill Speed – Crucial for effective cutting and preventing damage.
- ✓Drill Angle – Affects outcome and potential for damaging internal components.
- ✓Drill Placement – Strategic placement accesses the locking mechanism.
- ✓Drill Rigs – Provide stability and precision for accurate placement.
- ✓Dust Extraction – Removes shavings and debris to prevent interference.
Detailed Breakdown
| Aspect | Details | Notes |
|---|---|---|
| Pilot Hole Drilling | Start with a small bit to guide larger bits. | Prevents slipping and damage. |
| Carbide Drill Bits | Tungsten carbide bits known for hardness and durability. | Essential for hardened steel plates. |
| Cobalt Drill Bits | Offer better heat resistance than high-speed steel. | Suitable for moderately hardened materials. |
| Coolant Application | Apply cutting fluid or oil to the bit and surface. | Reduces friction, dissipates heat, and extends bit life. |
| Variable Speed Drills | Adjustable speed settings for optimal cutting. | Precise control prevents overheating. |
| Drill Bushings | Hardened steel guides to keep the bit on path. | Improves accuracy and prevents wandering. |
| Drill Rigs with Magnetic Bases | Securely attach for stability and precision. | Maintains consistent angle and depth. |
| Dust Collection Systems | Vacuum systems remove shavings and debris. | Prevents interference and contamination. |
Manipulation Techniques and Tools
Safe manipulation opens safes without drilling or significant damage. It requires understanding lock mechanisms and skill. Locksmiths feel for subtle movements and manipulate internal components.
Key Points
- ✓Scope Usage – Visually inspect the lock before manipulation.
- ✓Feeler Wires – Feel for the position of the lock’s tumblers.
- ✓Pick Guns – Rapidly vibrate pins to manipulate the lock.
- ✓Tension Wrenches – Apply pressure to manipulate pins.
- ✓Impressioning – Create a working key from lock impressions.
- ✓Dial Manipulation – Listen and feel for subtle movements to determine the combination.
- ✓Electronic Manipulation – Bypass or manipulate electronic components.
- ✓Lock Anatomy Knowledge – Understanding internal workings is essential.
Detailed Breakdown
| Aspect | Details | Notes |
|---|---|---|
| Scope Inspection | Examine internal components with a borescope. | Helps identify lock type and vulnerabilities. |
| Feeler Wire Manipulation | Feel for tumbler or lever positions with thin wires. | Requires a delicate touch and experience. |
| Pick Gun Application | Rapidly vibrate pins for manipulation. | Effective on certain pin tumbler locks. |
| Tension Wrench Usage | Apply rotational pressure to the cylinder. | Creates a binding effect for pin manipulation. |
| Impressioning Technique | File a blank key based on lock impressions. | A traditional method requiring patience. |
| Dial Listening | Listen for clicks and movements while turning. | Provides clues about the combination. |
| Electronic Bypass Tools | Bypass or manipulate electronic components. | Requires specialized knowledge. |
| Lock Anatomy Study | Understand internal workings of different locks. | Essential for successful manipulation. |
Autodialers and Electronic Safe Opening
Autodialers automate trying combinations. They’re useful when the combination is forgotten. Electronic techniques bypass or manipulate electronic components.
Key Points
- ✓Combination Guessing – Systematically try combinations.
- ✓Data Logging – Log tried combinations for analysis.
- ✓Electronic Bypass – Bypass security features.
- ✓Software Exploits – Exploit software vulnerabilities.
- ✓Hardware Hacking – Modify hardware to bypass the lock.
- ✓Power Surges – Disrupt electronic components.
- ✓Electromagnetic Pulses – Disable the lock.
- ✓Circuit Board Manipulation – Directly manipulate the circuit board.
Detailed Breakdown
| Aspect | Details | Notes |
|---|---|---|
| Combination Guessing Algorithm | Systematically try combinations. | Reduces time to open the safe. |
| Data Logging and Analysis | Log combinations for analysis. | Helps identify patterns. |
| Electronic Bypass Techniques | Bypass security features. | Requires specialized knowledge. |
| Software Vulnerability Exploitation | Exploit software vulnerabilities. | Requires advanced skills. |
| Hardware Modification | Modify hardware to bypass the lock. | Can be risky. |
| Power Surge Application | Disrupt electronic components. | Can damage electronics. |
| Electromagnetic Pulse (EMP) Usage | Disable the lock. | Requires specialized equipment. |
| Circuit Board Manipulation | Directly manipulate the circuit board. | Requires advanced skills. |
Dial Pullers and Spindle Manipulation
Dial pullers remove the dial to access the spindle. Spindle manipulation bypasses the lock. This requires a delicate touch and understanding of internal mechanisms.
Key Points
- ✓Dial Removal – Carefully remove the dial.
- ✓Spindle Access – Access the spindle after removal.
- ✓Spindle Manipulation – Manipulate the spindle to bypass the lock.
- ✓Feeler Gauges – Measure gaps between the spindle and lock mechanism.
- ✓Shim Placement – Place shims to manipulate the lock.
- ✓Listening Devices – Hear internal movements.
- ✓Tension Application – Apply tension while manipulating.
- ✓Lock Anatomy Knowledge – Understanding internal workings is essential.
Detailed Breakdown
| Aspect | Details | Notes |
|---|---|---|
| Dial Puller Attachment | Securely attach the puller to the dial. | Ensures a firm grip. |
| Dial Removal Process | Carefully remove the dial. | Requires patience. |
| Spindle Access Techniques | Access the spindle after dial removal. | May involve removing components. |
| Spindle Manipulation Tools | Manipulate the spindle. | Requires a delicate touch. |
| Feeler Gauge Measurement | Measure gaps between the spindle and mechanism. | Provides valuable information. |
| Shim Placement Strategies | Place shims to manipulate the lock. | Requires precise placement. |
| Listening Device Usage | Hear internal movements. | Helps identify bypass points. |
| Tension Application Methods | Apply tension while manipulating. | Creates a binding effect. |
Impressioning Tools and Techniques
Impressioning creates a working key by taking a lock impression. Insert a blank key, apply pressure, and file based on marks. It requires patience, skill, and understanding of lock mechanisms.
Key Points
- ✓Blank Key Selection – Choose the correct blank key.
- ✓Key Insertion – Insert and apply pressure.
- ✓Mark Analysis – Analyze marks left on the key.
- ✓Filing Techniques – Carefully remove material.
- ✓Repetition – Repeat the process until the key opens the lock.
- ✓Lock Lubrication – Ensure smooth operation.
- ✓Patience – Requires patience and detail.
- ✓Lock Anatomy Knowledge – Understanding internal workings is essential.
Detailed Breakdown
| Aspect | Details | Notes |
|---|---|---|
| Blank Key Identification | Identify the correct blank key. | Essential for success. |
| Key Insertion and Wiggling | Insert and wiggle to create marks. | Transfers internal features. |
| Mark Analysis and Interpretation | Analyze marks left on the key. | Requires a keen eye. |
| Filing with Precision Files | Carefully remove material. | Ensures accurate shaping. |
| Iterative Process of Filing and Testing | Repeat the process until the key works. | Requires patience. |
| Lock Lubrication for Smooth Operation | Lubricate the lock. | Reduces friction. |
| Patience and Persistence | Requires patience. | Success depends on observation. |
| Lock Anatomy Understanding | Understand internal workings. | Helps interpret marks. |
Bypass Tools and Techniques
Bypass tools circumvent the locking mechanism without significant damage. They exploit vulnerabilities. Bypass techniques require understanding lock mechanisms and skill.
Key Points
- ✓Shims – Manipulate internal components.
- ✓Wire Tools – Bypass pins or levers.
- ✓Lever Bypass Tools – Bypass lever locks.
- ✓Pin Tumbler Bypass Tools – Bypass pin tumbler locks.
- ✓Electronic Bypass Devices – Exploit electronic lock vulnerabilities.
- ✓Magnetic Bypass Tools – Manipulate internal components with magnets.
- ✓Listening Devices – Hear internal movements.
- ✓Lock Anatomy Knowledge – Understanding internal workings is essential.
Detailed Breakdown
| Aspect | Details | Notes |
|---|---|---|
| Shim Insertion Techniques | Manipulate internal components with shims. | Requires precise placement. |
| Wire Tool Manipulation | Bypass pins or levers with wires. | Effective on certain locks. |
| Lever Bypass Tool Application | Bypass lever locks. | Requires knowledge of lever locks. |
| Pin Tumbler Bypass Tool Usage | Bypass pin tumbler locks. | Effective on locks with weak points. |
| Electronic Bypass Device Implementation | Exploit electronic lock vulnerabilities. | Requires specialized knowledge. |
| Magnetic Bypass Tool Employment | Manipulate components with magnets. | Effective on susceptible locks. |
| Listening Device Utilization | Hear internal movements. | Helps identify bypass points. |
| Lock Anatomy Comprehension | Understand internal workings. | Helps identify vulnerabilities. |
Diagnostic Equipment for Safe Opening
Diagnostic equipment provides information about the lock and vulnerabilities. This includes scopes, listening devices, and electronic testers. It helps choose the most effective opening method and minimize damage.
Key Points
- ✓Scopes (Borescopes) – Visually inspect the interior.
- ✓Listening Devices – Hear internal movements.
- ✓Electronic Testers – Test electronic lock functionality.
- ✓Combination Analyzers – Analyze the combination.
- ✓X-Ray Machines – See internal components (rarely used).
- ✓Thermal Imaging Cameras – Detect heat signatures.
- ✓Ultrasonic Testers – Detect flaws in construction.
- ✓Lock Anatomy Knowledge – Understanding internal workings is essential.
Detailed Breakdown
| Aspect | Details | Notes |
|---|---|---|
| Borescope Inspection | Visually inspect the interior. | Helps identify bypass points. |
| Listening Device Application | Hear internal movements. | Helps identify the combination. |
| Electronic Tester Usage | Test electronic lock functionality. | Helps diagnose problems. |
| Combination Analyzer Employment | Analyze the combination. | Helps narrow down possibilities. |
| X-Ray Machine Application (Rare) | See internal components. | Rarely used due to safety. |
| Thermal Imaging Camera Utilization | Detect heat signatures. | Can identify hidden compartments. |
| Ultrasonic Tester Deployment | Detect flaws in construction. | Helps identify entry points. |
| Lock Anatomy Interpretation | Understand internal workings. | Helps select the opening method. |
Comparison Overview
| Item | Type | Pros | Cons | Best For |
|---|---|---|---|---|
| Drills | Destructive Entry | Effective, relatively quick. | Can damage the safe, requires precision. | Safes with unknown combinations. |
| Carbide Drill Bits | Drill Component | Cuts through hardened steel. | Expensive, can break. | Safes with anti-drill plates. |
| Borescopes | Diagnostic Tool | Non-destructive, visual inspection. | Requires access point, limited visibility. | Identifying lock mechanisms. |
| Manipulation Picks | Non-destructive Entry | No damage, can be quick. | Requires training, not effective on all safes. | Safes with known lock types. |
| Autodialers | Automated Entry | Automates guessing. | Time-consuming, not effective on all safes. | Safes with forgotten combinations. |
| Dial Pullers | Spindle Access | Provides spindle access. | Can damage the dial. | Safes where spindle manipulation is possible. |
| Impressioning Files | Key Creation | Creates a working key. | Requires skill, not effective on all locks. | Safes with simple locks. |
| Shims | Bypass Tool | Simple and inexpensive. | Limited effectiveness. | Safes with known vulnerabilities. |
| Tension Wrenches | Manipulation Tool | Essential for picking pin tumbler locks. | Requires skill. | Pin tumbler safe locks. |
| Pick Guns | Manipulation Tool | Can quickly open some locks. | Not effective on all locks. | Pin tumbler safe locks. |
| Electronic Testers | Diagnostic Tool | Tests electronic locks. | Requires knowledge of electronics. | Electronic safe locks. |
| Listening Devices | Diagnostic Tool | Helps hear lock movements. | Requires quiet, skill to interpret. | Mechanical safe locks. |
| Magnetic Bypass Tools | Bypass Tool | Can manipulate components. | Limited effectiveness. | Safes susceptible to magnetic interference. |
| Lever Bypass Tools | Bypass Tool | Specialized for lever locks. | Requires knowledge of lever locks. | Lever safe locks. |
Frequently Asked Questions
What does a locksmith do?
Locksmiths provide services related to locks and security. They install, repair, and open locks for homes, businesses, and vehicles. They also offer key duplication, safe opening, and security system installation.
How much does a locksmith cost?
Locksmith costs vary based on the service, time, and location. Key duplication may cost around $20. Safe opening or emergency lockout can range from $100 to $500 or more. Get a quote beforehand.
Is it legal to open a safe without the combination?
Yes, a licensed locksmith can open a safe without the combination with the owner’s permission. Locksmiths use techniques to open safes without significant damage.
How long does it take a locksmith to open a safe?
The time varies based on the safe type, lock complexity, and method used. Simple safes may take minutes. Complex safes could take hours or days using non-destructive methods.
What is the most common reason for needing a safe opened?
The most common reason is a forgotten combination. People forget their safe combination and need a locksmith to regain access.
Can I open my safe myself without a locksmith?
It’s not recommended. You could damage the safe and its contents. It’s best to hire a professional.
What should I look for when hiring a locksmith for safe opening?
Look for a licensed, insured, and experienced locksmith. Check credentials, read reviews, and ask for references. Ensure they have the tools to open your safe without damage.
What are the ethical considerations for a locksmith opening a safe?
Ethical locksmiths prioritize security and privacy. They verify ownership before opening a safe. They maintain confidentiality and adhere to professional standards.

Contact Locksmith For London Today
Looking for safe opening and locksmith services in London? Contact Locksmith For London for expert assistance. We also provide 24/7 emergency services and affordable solutions across London.